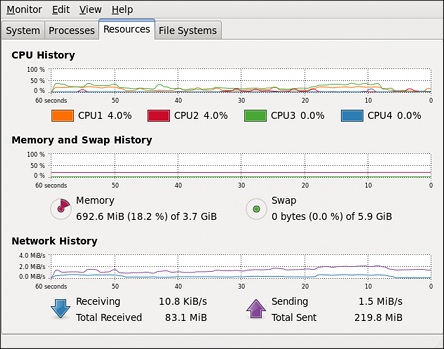
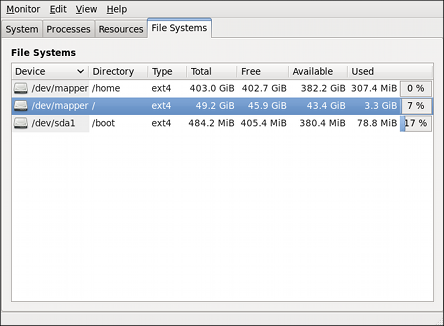
Part I. Package Management
Table of Contents
- 1. Yum
- 2. PackageKit
- 3. RPM
Chapter 1. Yum
Secure Package Management with GPG-Signed Packages
1.1. Checking For and Updating Packages
1.1.1. Checking For Updates
yum check-update command to see which installed packages on your system have updates available.
Note: Yum and Superuser Privileges
yum
to install, update or remove packages on your system. All examples in
this chapter assume that you have already obtained superuser privileges
by using either the su or sudo command.
~]# yum check-update
Loaded plugins: presto, refresh-packagekit, security
PackageKit.x86_64 0.5.8-2.el6 rhel
PackageKit-glib.x86_64 0.5.8-2.el6 rhel
PackageKit-yum.x86_64 0.5.8-2.el6 rhel
PackageKit-yum-plugin.x86_64 0.5.8-2.el6 rhel
glibc.x86_64 2.11.90-20.el6 rhel
glibc-common.x86_64 2.10.90-22 rhel
kernel.x86_64 2.6.31-14.el6 rhel
kernel-firmware.noarch 2.6.31-14.el6 rhel
rpm.x86_64 4.7.1-5.el6 rhel
rpm-libs.x86_64 4.7.1-5.el6 rhel
rpm-python.x86_64 4.7.1-5.el6 rhel
udev.x86_64 147-2.15.el6 rhel
yum.noarch 3.2.24-4.el6 rhel
PackageKit— the name of the packagex86_64— the CPU architecture the package was built for0.5.8— the version of the updated package to be installedrhel— the repository in which the updated package is located
yum and rpm packages), as well as their dependencies (such as the kernel-firmware, rpm-libs and rpm-python packages), all using yum.
1.1.2. Updating Packages
yum update <package_name>:
~]# yum update udev
Loaded plugins: presto, refresh-packagekit, rhnplugin, security
Setting up Update Process
Resolving Dependencies
--> Running transaction check
---> Package udev.x86_64 0:147-2.15.el6 set to be updated
--> Finished Dependency Resolution
Dependencies Resolved
===========================================================================
Package Arch Version Repository Size
===========================================================================
Updating:
udev x86_64 147-2.15.el6 rhel 337 k
Transaction Summary
===========================================================================
Install 0 Package(s)
Upgrade 1 Package(s)
Total download size: 337 k
Is this ok [y/N]:
Loaded plugins: presto, refresh-packagekit, security—yumalways informs you which Yum plugins are installed and enabled. Here,yumis using the presto, refresh-packagekit and security plugins. Refer to Section 1.4, “Yum Plugins” for general information on Yum plugins, or to Section 1.4.3, “Plugin Descriptions” for descriptions of specific plugins.kernel.x86_64— you can download and install new kernels safely withyum.Important: Updating and Installing Kernels with Yum
yumalways installs a new kernel in the same sense that RPM installs a new kernel when you use the commandrpm -i kernel. Therefore, you do not need to worry about the distinction between installing and upgrading a kernel package when you useyum: it will do the right thing, regardless of whether you are using theyum updateoryum installcommand.When using RPM, on the other hand, it is important to use therpm -i kernelcommand (which installs a new kernel) instead ofrpm -u kernel(which replaces the current kernel). Refer to Section 3.2.2, “Installing and Upgrading” for more information on installing/updating kernels with RPM.yumpresents the update information and then prompts you as to whether you want it to perform the update;yumruns interactively by default. If you already know which transactionsyumplans to perform, you can use the-yoption to automatically answeryesto any questionsyummay ask (in which case it runs non-interactively). However, you should always examine which changesyumplans to make to the system so that you can easily troubleshoot any problems that might arise.If a transaction does go awry, you can view Yum's log of transactions by enteringcat /var/log/yum.logat the shell prompt. The most recent transactions are listed at the end of the log file.
Updating All Packages and Their Dependencies
yum update (without any arguments):
Example 1.1. Updating all packages at once
~]# yum update1.1.3. Updating Security-Related Packages
yum command with a set of highly-useful security-centric commands, subcommands and options. Refer to Section 1.4.3, “security (yum-plugin-security)” for specific information.
1.1.4. Preserving Configuration File Changes
1.2. Packages and Package Groups
1.2.1. Searching, Listing and Displaying Package Information
yum search <term> [more_terms] command. yum displays the list of matches for each term:
~]# yum search meld kompare
Loaded plugins: presto, refresh-packagekit, rhnplugin, security
============================ Matched: kompare =============================
kdesdk.x86_64 : The KDE Software Development Kit (SDK)
Warning: No matches found for: meld
yum search is useful for searching for packages you do not know the name of, but for which you know a related term.
Listing Packages
Tip: Filtering Results with Glob Expressions
* (which expands to match any character multiple times) and ?
(which expands to match any one character). Be careful to escape both
of these glob characters when passing them as arguments to a yum command. If you do not, the bash shell will interpret the glob expressions as pathname expansions, and potentially pass all files in the current directory that match the globs to yum, which is not what you want. Instead, you want to pass the glob expressions themselves to yum, which you can do by either:
- escaping the wildcard characters
- double-quoting or single-quoting the entire glob expression.
Example 1.2. Filtering results using a single glob expression with two escaped wildcard characters
~]# yum list available gstreamer\*plugin\*
Loaded plugins: presto, refresh-packagekit, rhnplugin, security
Available Packages
gstreamer-plugins-bad-free.i686 0.10.17-4.el6 rhel
gstreamer-plugins-base.i686 0.10.26-1.el6 rhel
gstreamer-plugins-base-devel.i686 0.10.26-1.el6 rhel
gstreamer-plugins-base-devel.x86_64 0.10.26-1.el6 rhel
gstreamer-plugins-good.i686 0.10.18-1.el6 rhel
Example 1.3. Filtering results using a double-quoted glob expression
~]# yum list installed "krb?-*"
Loaded plugins: presto, refresh-packagekit, rhnplugin, security
Installed Packages
krb5-libs.x86_64 1.8.1-3.el6 @rhel
krb5-workstation.x86_64 1.8.1-3.el6 @rhel
yum list— List information on installed and available packages matching all glob expressions.<glob_expr>[more_glob_exprs]Example 1.4. Listing all ABRT addons and plugins using glob expressions
~]#
yum list abrt-addon\* abrt-plugin\*Loaded plugins: presto, refresh-packagekit, rhnplugin, security Installed Packages abrt-addon-ccpp.x86_64 1.0.7-5.el6 @rhel abrt-addon-kerneloops.x86_64 1.0.7-5.el6 @rhel abrt-addon-python.x86_64 1.0.7-5.el6 @rhel abrt-plugin-bugzilla.x86_64 1.0.7-5.el6 @rhel abrt-plugin-logger.x86_64 1.0.7-5.el6 @rhel abrt-plugin-sosreport.x86_64 1.0.7-5.el6 @rhel abrt-plugin-ticketuploader.x86_64 1.0.7-5.el6 @rhel
Displaying Package Info
yum info <package_name> [more_names]
displays information about one or more packages (glob expressions are valid here as well):
~]# yum info abrt
Loaded plugins: presto, refresh-packagekit, rhnplugin, security
Installed Packages
Name : abrt
Arch : x86_64
Version : 1.0.7
Release : 5.el6
Size : 578 k
Repo : installed
From repo : rhel
Summary : Automatic bug detection and reporting tool
URL : https://fedorahosted.org/abrt/
License : GPLv2+
Description: abrt is a tool to help users to detect defects in applications
: and to create a bug report with all informations needed by
: maintainer to fix it. It uses plugin system to extend its
: functionality.
yum info <package_name> is similar to the rpm -q --info <package_name> command, but provides as additional information the ID of the Yum repository the RPM package is found in (look for the From repo: line in the output).
yumdb info <package_name> [more_names] can be used to query the Yum
database for alternative and useful information about a package,
including the checksum of the package (and algorithm used to produce it,
such as SHA-256), the command given on the command line that was
invoked to install the package (if any), and the reason that the package
is installed on the system (where user indicates it was installed by the user, and dep means it was brought in as a dependency):
~]# yumdb info yum
yum-3.2.27-4.el6.noarch
checksum_data = 15c8eaf583fabad6974a35b9f6c6527e49362fe4e23baec1682ef51a598e4abb
checksum_type = sha256
command_line = update
from_repo = rhel
from_repo_revision = 1271991599
from_repo_timestamp = 1271991721
reason = user
releasever = 6man yumdb for more information on the yumdb command.
yum history command, which is new in Red Hat Enterprise Linux 6, can be used to show a timeline of Yum
transactions, the dates and times on when they occurred, the number of
packages affected, whether transactions succeeded or were aborted, and
if the RPM database was changed between transactions. Refer to the history section of man yum for details.
1.2.2. Installing
~]# yum install <package_name> yum install <package_name> [more_names] .
.arch to the package name:
~]# yum install sqlite2.i586~]# yum install audacious-plugins-\*yum install. If you know the name of the binary you want to install, but not its package name, you can give yum install the path name:
~]# yum install /usr/sbin/namedyum then searches through its package
lists, finds the package which provides /usr/sbin/named, if any, and
prompts you as to whether you want to install it.
named binary, but don't know in which bin or sbin directory that file lives? In that situation, you can give yum provides a glob expression:
Example 1.5. Finding which package owns a file and installing it
~]#yum provides "*bin/named"Loaded plugins: presto, refresh-packagekit, rhnplugin, security 32:bind-9.7.0-4.P1.el6.x86_64 : The Berkeley Internet Name Domain (BIND) : DNS (Domain Name System) server Repo : rhel Matched from: Filename : /usr/sbin/named ~]#yum install bind
Note
yum provides is the same as yum whatprovides.
Tip: yum provides/whatprovides and Glob Expressions
yum provides "*/<file_name>" is a common and useful trick to quickly find the package(s) that contain <file_name>.
Installing a Package Group
yum grouplist -v command lists the names of all package groups, and, next to each of them, their groupid in parentheses. The groupid is always the term in the last pair of parentheses, such as kde-desktop and kde-software-development in this example:
Not all packages used in examples may be available on RHN
~]# yum -v grouplist kde\*
KDE (K Desktop Environment) (kde-desktop)
KDE Software Development (kde-software-development)
groupinstall:
~]# yum groupinstall "KDE (K Desktop Environment)"~]# yum groupinstall kde-desktopinstall command if you prepend it with an @-symbol (which tells yum that you want to perform a groupinstall):
~]# yum install @kde-desktop1.2.3. Removing
yum remove <package_name>
uninstalls (removes in RPM and Yum
terminology) the package, as well as any packages that depend on it. As
when you install multiple packages, you can remove several at once by
adding more package names to the command:
yum remove foo bar bazinstall, remove can take these arguments:
- package names
- glob expressions
- file lists
- package provides
Warning: Removing a Package when Other Packages Depend On It
Removing a Package Group
install syntax.
Example 1.6. Alternative but equivalent ways of removing a package group
~]#yum groupremove "KDE (K Desktop Environment)"~]#yum groupremove kde-desktop~]#yum remove @kde-desktop
Smart package group removal
yum to remove only those packages which are not required by any other packages or groups by adding the groupremove_leaf_only=1 directive to the [main] section of the /etc/yum.conf configuration file. For more information on this directive, refer to Section 1.3.1, “Setting [main] Options”.
1.3. Configuring Yum and Yum Repositories
- set global Yum options by editing the
[main]section of the/etc/yum.confconfiguration file; - set options for individual repositories by editing the [
repository] sections in/etc/yum.confand.repofiles in the/etc/yum.repos.d/directory; - use Yum variables in
/etc/yum.confand files in/etc/yum.repos.d/so that dynamic version and architecture values are handled correctly; and, - set up your own custom Yum repository.
/etc/yum.conf configuration file contains one mandatory [main] section under which you can set Yum options. The values that you define in the [main] section of yum.conf have global effect, and may override values set any individual [repository] sections. You can also add [repository] sections to /etc/yum.conf; however, best practice is to define individual repositories in new or existing .repo files in the /etc/yum.repos.d/directory. Refer to Section 1.3.2, “Setting [repository] Options” if you need to add or edit repository-specific information.
1.3.1. Setting [main] Options
/etc/yum.conf configuration file contains exactly one [main] section. You can add many additional options under the [main] section heading in /etc/yum.conf. Some of the key-value pairs in the [main] section affect how yum operates; others affect how Yum treats repositories. The best source of information for all Yum options is in the [main] OPTIONS and [repository] OPTIONS sections of man yum.conf.
/etc/yum.conf configuration file:
[main]
cachedir=/var/cache/yum/$basearch/$releasever
keepcache=0
debuglevel=2
logfile=/var/log/yum.log
exactarch=1
obsoletes=1
gpgcheck=1
plugins=1
installonly_limit=3
[comments abridged]
# PUT YOUR REPOS HERE OR IN separate files named file.repo
# in /etc/yum.repos.d
[main] section, and descriptions for each:
- assumeyes=
<value> - ...where
<value>is one of:0—yumshould prompt for confirmation of critical actions it performs. This is the default.1— Do not prompt for confirmation of criticalyumactions. Ifassumeyes=1is set,yumbehaves in the same way that the command line option-ydoes. - cachedir=
/var/cache/yum/$basearch/$releasever - This option specifies the directory where Yum should store its cache and database files. By default, Yum's cache directory is
/var/cache/yum/$basearch/$releasever. See Section 1.3.3, “Using Yum Variables” for descriptions of the$basearchand$releaseverYum variables. - debuglevel=
value - ...where
<value>is an integer between1and10. Setting a higherdebuglevelvalue causesyumto display more detailed debugging output.debuglevel=0disables debugging output, whiledebuglevel=2is the default. - exactarch=
<value> - ...where
<value>is one of:0— Do not take into account the exact architecture when updating packages.1— Consider the exact architecture when updating packages. With this setting,yumwill not install an i686 package to update an i386 package already installed on the system. This is the default. - exclude=
<package_name>[more_package_names] - This option allows you to exclude packages by keyword during installation/updates. Listing multiple packages for exclusion can be accomplished by quoting a space-delimited list of packages. Shell globs using wildcards (for example,
*and?) are allowed. - gpgcheck=
<value> - ...where
<value>is one of:0— Disable GPG signature-checking on packages in all repositories, including local package installation.1— Enable GPG signature-checking on all packages in all repositories, including local package installation.gpgcheck=1is the default, and thus all packages' signatures are checked.If this option is set in the[main]section of the/etc/yum.conffile, it sets the GPG-checking rule for all repositories. However, you can also setgpgcheck=<value>for individual repositories instead; i.e., you can enable GPG-checking on one repository while disabling it on another. Settinggpgcheck=for an individual repository in its correpsonding<value>.repofile overrides the default if it is present in/etc/yum.conf. Refer to Section 3.3, “Checking a Package's Signature” for further information on GPG signature-checking. - groupremove_leaf_only=
<value> - ...where
<value>is one of:0—yumshould not check the dependencies of each package when removing a package group. With this setting,yumremoves all packages in a package group, regardless of whether those packages are required by other packages or groups.groupremove_leaf_only=0is the default.1—yumshould check the dependencies of each package when removing a package group, and remove only those packages which are not not required by any other package or group.For more information on removing packages, refer to Smart package group removal. - installonlypkgs=
<space><separated><list><of><packages> - Here you can provide a space-separated list of packages which
yumcan install, but will never update. Refer toman yum.conffor the list of packages which are install-only by default. If you add theinstallonlypkgsdirective to/etc/yum.conf, you should ensure that you list all of the packages that should be install-only, including any of those listed under theinstallonlypkgssection ofman yum.conf. In particular, kernel packages should always be listed ininstallonlypkgs(as they are by default), andinstallonly_limitshould always be set to a value greater than2so that a backup kernel is always available in case the default one fails to boot. Refer to installonly_limit=<value>for details on theinstallonly_limitdirective. - installonly_limit=
<value> - ...where
<value>is an integer representing the maximum number of versions that can be installed simultaneously for any single package listed in theinstallonlypkgsdirective. The defaults for theinstallonlypkgsdirective include several different kernel packages, so be aware that changing the value ofinstallonly_limitwill also affect the maximum number of installed versions of any single kernel package. The default value listed in/etc/yum.confisinstallonly_limit=3, and it is not recommended to decrease this value, particularly below2. - keepcache=
<value> - ...where value is one of:
0— Do not retain the cache of headers and packages after a successful installation. This is the default.1— Retain the cache after a successful installation. - logfile=
/var/log/yum.log - This option specifies where
yumshould send its logging output. By default,yumlogs to/var/log/yum.log. - multilib_policy=
<value> - ...where
<value>is one of:best— install the best-choice architecture for this system. For example, settingmultilib_policy=beston an AMD64 system causesyumto install 64-bit versions of all packages.all— always install every possible architecture for every package. For example, withmultilib_policyset toallon an AMD64 system,yumwould install both the i586 and AMD64 versions of a package, if both were available. - obsoletes=
<value> - ...where
<value>is one of:0— Disableyum's obsoletes processing logic when performing updates.1— Enableyum's obsoletes processing logic when performing updates. When one package declares in its spec file that it obsoletes another package, the latter package will be replaced by the former package when the former package is installed. Obsoletes are declared, for example, when a package is renamed.obsoletes=1the default. - plugins=
<value> - ...where
<value>is one of:0— Disable all Yum plugins globally.Disabling plugins is not advised
Disabling all plugins is not advised because certain plugins provide importantYumservices. In particular, rhnplugin enables connecting toRed Hat Network, and the security plugin allows system administrators to easily update the system with (sometimes critical) security updates. Disabling plugins globally is provided as a convenience option, and is generally only recommended when diagnosing a potential problem withYum.1— Enable all Yum plugins globally. Withplugins=1, you can still disable a specific Yum plugin by settingenabled=0in that plugin's configuration file. Refer to Section 1.4, “Yum Plugins” for more information about various Yum plugins, or to Section 1.4.1, “Enabling, Configuring and Disabling Yum Plugins” for further information on controlling plugins. - reposdir=
</absolute/path/to/directory/containing/repo/files> - This option allows you to specify a directory where
.repofiles are located. All.repofiles contain repository information (similar to the [repository] section(s) of/etc/yum.conf).yumcollects all repository information from.repofiles and the [repository] section of the/etc/yum.conffile to create a master list of repositories to use for transactions. Refer to Section 1.3.2, “Setting [repository] Options” for more information about options you can use for both the [repository] section and.repofiles. Ifreposdiris not set,yumuses the default directory/etc/yum.repos.d/. - retries=
<value> - ...where
<value>is an integer0or greater. This value sets the number of timesyumshould attempt to retrieve a file before returning an error. Setting this to0makesyumretry forever. The default value is10.
1.3.2. Setting [repository] Options
repository] sections (where repository is a unique repository ID, such as [my_personal_repo]) to /etc/yum.conf or to .repo files in the /etc/yum.repos.d/directory. All .repo files in /etc/yum.repos.d/are read by yum; best practice is to define your repositories here instead of in /etc/yum.conf. You can create new, custom .repo files in this directory, add [repository] sections to those files, and the next time you run a yum command, it will take all newly-added repositories into account.
.repo file should take:
[repository_ID] name=A Repository Name baseurl=http://path/to/repo or ftp://path/to/repo or file://path/to/local/repo
repository] section must contain the following minimum parts:
- [
repository_ID] - The repository ID is a unique, one-word (no spaces; underscores are allowed) string of characters (enclosed by brackets) that serves as a repository identifier.
- name=
<My Repository Name> - This is a human-readable string describing the repository.
- baseurl=http://path/to/repo, ftp://path/to/repo, file://path/to/local/repo
- This is a URL to the directory where the repodata directory of a repository is located. Usually this URL is an HTTP link, such as:
baseurl=http://path/to/repo/releases/$releasever/server/$basearch/os/
Yum always expands the$releasever,$archand$basearchvariables in URLs. See the following section for explanations of all Yum variables: Section 1.3.3, “Using Yum Variables”.- If the repository is available over FTP, use: ftp://path/to/repo
- If the repository is local to the machine, use file://path/to/local/repo
- If a specific online repository requires basic HTTP authentication, you can specify your username and password in the
http://path/to/repoby prepending it asusername:password@link. For example, if a repository on http://www.example.com/repo/ requires a username of "user" and a password of "password", then thebaseurllink could be specified as:baseurl=http://
user:password@www.example.com/repo/
repository] directive:
- enabled=
<value> - ...where
<value>is one of:0— do not include this repository as a package source when performing updates and installs. This is an easy way of quickly turning repositories on and off, which is useful when you desire a single package from a repository that you do not want to enable for updates or installs.1— include this repository as a package source.Turning repositories on and off can also be performed quickly by passing either the--enablerepo=<orrepo_name>--disablerepo=<option torepo_name>yum, or easily through PackageKit's Add/Remove Software window.
repository] options exist. Refer to the [repository] OPTIONS section of man yum.conf for the exhaustive list and descriptions for each.
1.3.3. Using Yum Variables
yum commands and in all Yum configuration files (/etc/yum.conf and all .repo files in /etc/yum.repos.d/.
-
$releasever - You can use this variable to reference the release version of Red Hat Enterprise Linux. Yum obtains the value of
$releaseverfrom thedistroverpkg=<value>line in the/etc/yum.confconfiguration file. If there is no such line in/etc/yum.conf, thenyuminfers the correct value by deriving the version number from theredhat-releasepackage. -
$arch - You can use this variable to refer to the system's CPU architecture as returned when calling Python's
os.uname()function. Valid values for$archinclude:i586,i686andx86_64. -
$basearch - You can use
$basearchto reference the base architecture of the system. For example, i686 and i586 machines both have a base architecture ofi386, and AMD64 and Intel64 machines have a base architecture ofx86_64. -
$YUM0-9 - These ten variables are each replaced with the value of any shell environment variables with the same name. If one of these variables is referenced (in
/etc/yum.conffor example) and a shell environment variable with the same name does not exist, then the configuration file variable is not replaced.
1.3.4. Creating a Yum Repository
Procedure 1.1. Setting Up a Yum repository
- Install the
createrepopackage:~]#
yum install createrepo - Copy all of the packages into one directory, such as
/mnt/local_repo/. - Run the
createrepo --databasecommand on that directory:~]#
createrepo --database /mnt/local_repoImportant
Because RPM packages for Red Hat Enterprise Linux 6 are compressed using the XZ lossless data compression format, and may also be signed using alternative (and stronger) hash algorithms such as SHA-256, it is not possible to runcreaterepoon Red Hat Enterprise Linux 5 to create the package metadata for Red Hat Enterprise Linux 6 packages. Thecreaterepocommand relies onrpmto open and inspect the packages, andrpmon Red Hat Enterprise Linux 5 is not able to open the improved Red Hat Enterprise Linux 6 RPM package format.
yum operations.
1.4. Yum Plugins
yum command:
~]# yum info yum
Loaded plugins: presto, refresh-packagekit, security
[output truncated]Loaded plugins are the names you can provide to the --disableplugins=<plugin_name> option.
1.4.1. Enabling, Configuring and Disabling Yum Plugins
plugins= is present in the [main] section of /etc/yum.conf, and that its value is set to 1:
plugins=1
plugins=0.
Disabling plugins is not advised
Yum services. In particular, rhnplugin enables connecting to Red Hat Network,
and the security plugin allows system administrators to easily update
the system with (sometimes critical) security updates. Disabling plugins
globally is provided as a convenience option, and is generally only
recommended when diagnosing a potential problem with Yum.
/etc/yum/pluginconf.d/ directory. You can set plugin-specific options in these files. For example, here is the security plugin's security.conf configuration file:
Example 1.7. A minimal Yum plugin configuration file
[main] enabled=1
[main] section (similar to Yum's /etc/yum.conf file) in which there is (or you can place if it is missing) an enabled= option that controls whether the plugin is enabled when you run yum commands.
enabled=0 in /etc/yum.conf, then all plugins are disabled regardless of whether they are enabled in their individual configuration files.
yum command, use the --noplugins option.
yum command, then you can add the --disableplugin=<plugin_name> option to the command:
Example 1.8. Disabling the presto plugin while running yum update
~]# yum update --disableplugin=presto--disableplugin= option are the same names listed after the Loaded plugins: line in the output of any yum
command. You can disable multiple plugins by separating their names
with commas. In addition, you can match multiple similarly-named plugin
names or simply shorten long ones by using glob expressions: --disableplugin=presto,refresh-pack*.
1.4.2. Installing More Yum Plugins
yum-plugin-<plugin_name> package-naming convention, but not always: the package which provides the presto plugin is named yum-presto, for example. You can install a Yum plugin in the same way you install other packages:
~]# yum install yum-plugin-security1.4.3. Plugin Descriptions
presto (yum-presto)
protect-packages (yum-plugin-protect-packages)
yum
package and all packages it depends on from being purposefully or
accidentally removed. This simple scheme prevents many of the most
important packages necessary for your system to run from being removed.
In addition, you can list more packages, one per line, in the /etc/sysconfig/protected-packages file[1] (which you should create if it does not exist), and protect-packages will extend protection-from-removal to those packages as well. To temporarily override package protection, use the --override-protection option with an applicable yum command.
rhnplugin (yum-rhn-plugin)
Red Hat Network (RHN). Systems registered with RHN are able to update and install packages from Red Hat Network.
man rhnplugin for more information.
refresh-packagekit (PackageKit-yum-plugin)
security (yum-plugin-security)
yum with a set of highly-useful security-related commands, subcommands and options.
~]# yum check-update --security
Loaded plugins: presto, refresh-packagekit, security
Limiting package lists to security relevant ones
Needed 3 of 7 packages, for security
elinks.x86_64 0.12-0.13.el6 rhel
kernel.x86_64 2.6.30.8-64.el6 rhel
kernel-headers.x86_64 2.6.30.8-64.el6 rhelyum update --security or yum update-minimal --security
to update those packages which are affected by security advisories.
Both of these commands update all packages on the system for which a
security advisiory has been issued. yum update-minimal --security updates them to the latest packages which were released as part of a security advisory, while yum update --security will update all packages affected by a security advisory to the latest version of that package available.
- the kernel-2.6.30.8-16 package is installed on your system;
- the kernel-2.6.30.8-32 package was released as a security update;
- then kernel-2.6.30.8-64 was released as a bug fix update,
yum update-minimal --security will update you to kernel-2.6.30.8-32, and yum update --security will update you to kernel-2.6.30.8-64. Conservative system administrators may want to use update-minimal to reduce the risk incurred by updating packages as much as possible.
man yum-security for usage details and further explanation of the enhancements the security plugin adds to yum.
1.5. Additional Resources
- The Yum home page and wiki — http://yum.baseurl.org/wiki/Guides
- The
Yum Guidessection of the wiki contains more Yum documentation. - Managing Software with Yum — http://docs.fedoraproject.org/en-US/Fedora_Core/5/html-single/Software_Management_Guide/
- A useful resource that provides additional information about using the Yum package manager.
[1]
You can also place files with the extension .list in the /etc/sysconfig/protected-packages.d/ directory (which you should create if it does not exist), and list packages—one per line—in these files. protect-packages will protect these too.
Chapter 2. PackageKit
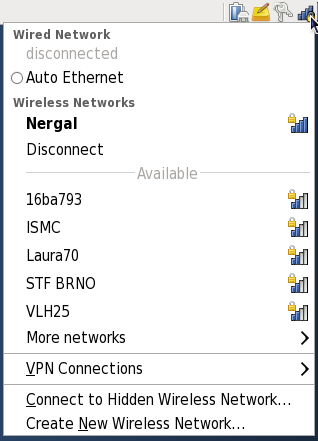
2.1. Updating Packages with Software Update
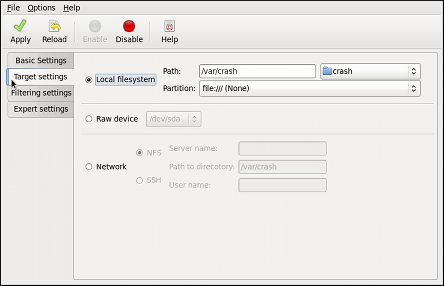
gpk-update-viewer command at the shell prompt. In the Software Updates window, all available updates are listed along with the names of the packages being updated (minus the .rpm
suffix, but including the CPU architecture), a short summary of the
package, and, usually, short descriptions of the changes the update
provides. Any updates you do not wish to install can be de-selected here
by unchecking the checkbox corresponding to the update.
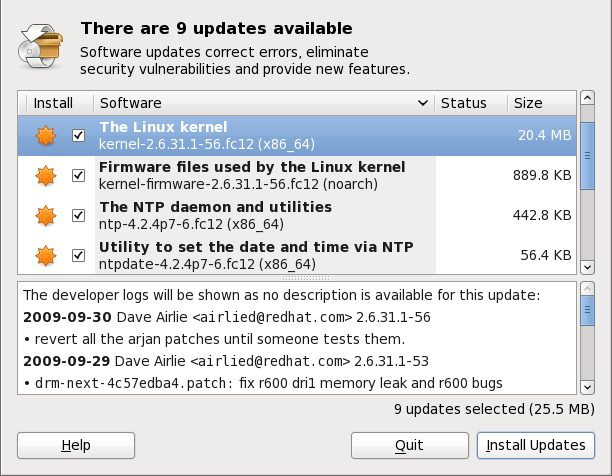
Figure 2.1. Installing updates with Software Update
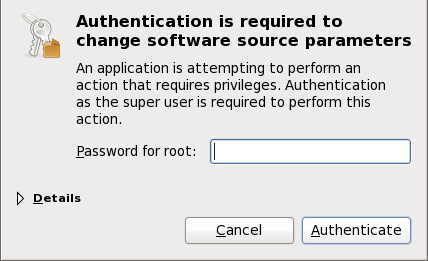
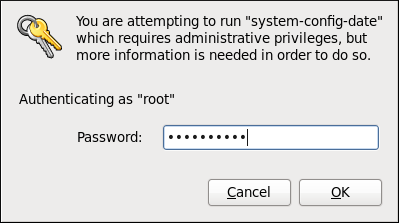
Figure 2.2. PackageKit uses PolicyKit to authenticate
kernel
package, then it will prompt you after installation, asking you whether
you want to reboot the system and thereby boot into the newly-installed
kernel.
Setting the Update-Checking Interval
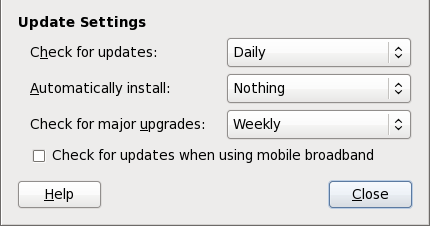
Figure 2.3. Setting PackageKit's update-checking interval
2.2. Using Add/Remove Software
gpk-application command at the shell prompt.
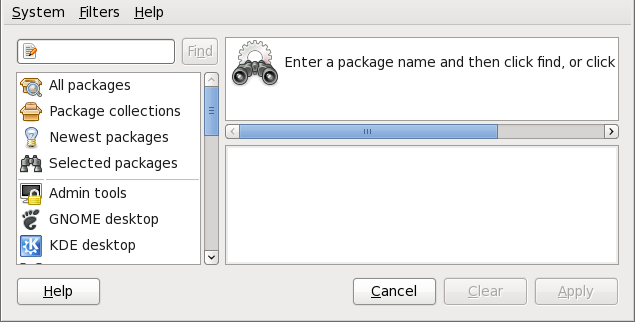
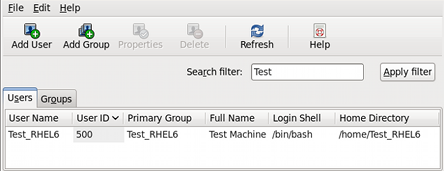
Figure 2.4. PackageKit's Add/Remove Software window
2.2.1. Refreshing Software Sources (Yum Repositories)
name=<My Repository Name> field of all [repository] sections in the /etc/yum.conf configuration file, and in all repository.repo/etc/yum.repos.d/ directory.
enabled=<1 or 0> field in [repository]
sections. Checking an unchecked box enables the Yum repository, and
unchecking it disables it. Performing either function causes PolicyKit to prompt for superuser authentication to enable or disable the repository. PackageKit actually inserts the enabled=<1 or 0> line into the correct [repository] section if it does not exist, or changes the value if it does. This means that enabling or disabling a repository through the Software Sources
window causes that change to persist after closing the window or
rebooting the system. The ability to quickly enable and disable
repositories based on our needs is a highly-convenient feature of PackageKit.
Showing Source RPM, Test and Debuginfo Repositories
2.2.2. Finding Packages with Filters
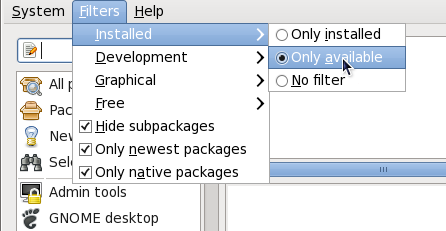
Figure 2.5. Filtering out already-installed packages
<package_name>-devel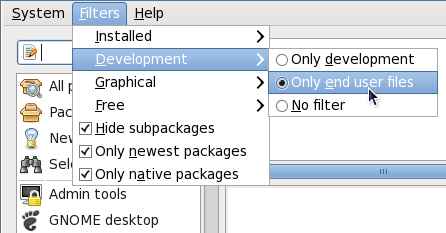
Figure 2.6. Filtering out development packages from the list of Find results
- Narrows the search to either applications which provide a GUI interface or those that do not (). This filter is useful when browsing for GUI applications that perform a specific function.
- Search for packages which are considered to be free software Refer to the Fedora Licensing List for details on approved licenses.
- Checking the checkbox filters out generally-uninteresting packages that are typically only dependencies of other packages that we want. For example, checking and searching for
<package><package>-devel<package>-libs<package>-libs-devel<package>-debuginfo
- Checking filters out all older versions of the same package from the list of results, which is generally what we want.
Important: Using the Only newest items filter
Checking filters out all but the most recent version of any package from the results list. This filter is often combined with the filter to search for the latest available versions of new (not installed) packages. - Only native packages
- Checking the box on a multilib system causes PackageKit to omit listing results for packages compiled for the architecture that runs in compatibility mode. For example, enabling this filter on a 64-bit system with an AMD64 CPU would cause all packages built for the 32-bit x86 CPU architecture not to be shown in the list of results, even though those packages are able to run on an AMD64 machine. Packages which are architecture-agnostic (i.e. noarch packages such as
crontabs-1.10-32.1.el6.noarch.rpm) are never filtered out by checking . This filter has no affect on non-multilib systems, such as x86 machines.
2.2.3. Installing and Removing Packages (and Dependencies)
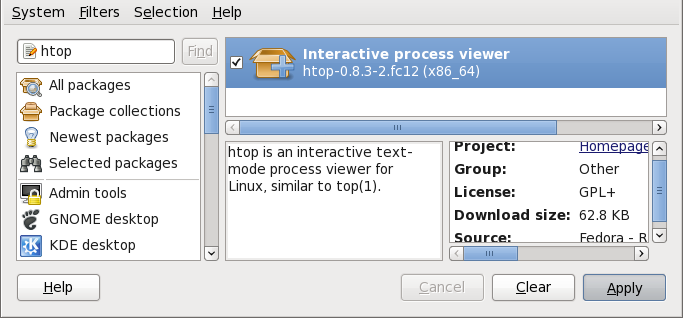
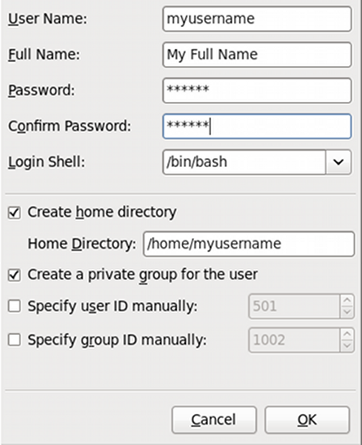
Figure 2.7. Viewing and installing a package with PackageKit's Add/Remove Software window
htop, an colorful and enhanced version of the top process viewer, by opening a shell prompt and entering:
~]$ htop
top is good enough for us and we want to uninstall it. Remembering that we need to change the filter we recently used to install it to in → , we search for htop
again and uncheck it. The program did not install any dependencies of
its own; if it had, those would be automatically removed as well, as
long as they were not also dependencies of any other packages still
installed on our system.
Warning: Removing a Package when Other Packages Depend On It
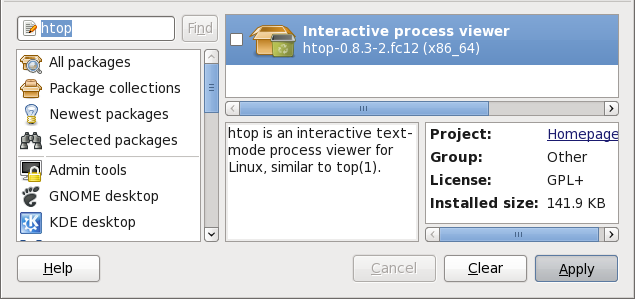
Figure 2.8. Removing a package with PackageKit's Add/Remove Software window
2.2.4. Installing and Removing Package Groups
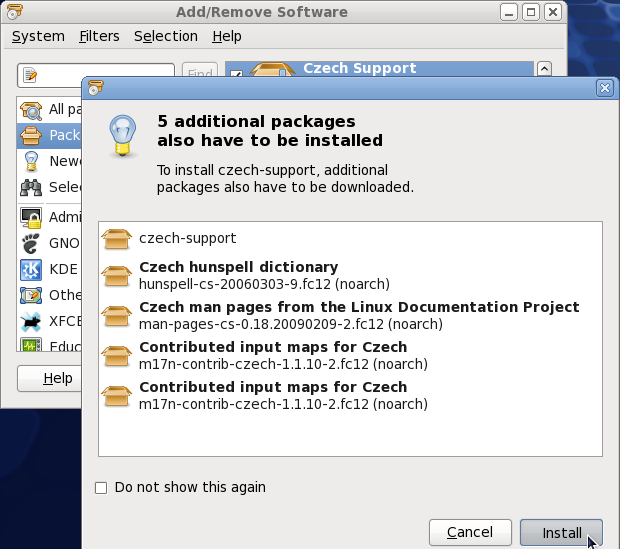
Figure 2.9. Installing the Czech Support package group
2.2.5. Viewing the Transaction Log
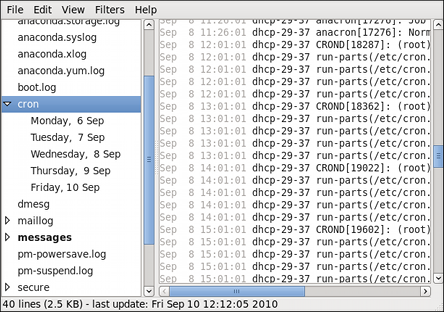
gpk-log command at the shell prompt.
Updated System or Installed Packages, the Date on which that action was performed, the Username of the user who performed the action, and the front end Application the user used (such as Update Icon, or kpackagekit). The Details column provides the types of the transactions, such as Updated, Installed or Removed, as well as the list of packages the transactions were performed on.
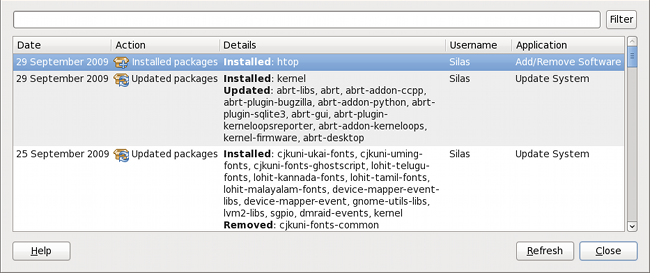
Figure 2.10. Viewing the log of package management transactions with the Software Log Viewer
2.3. PackageKit Architecture
packagekitd daemon back end, which communicates with a package manager-specific back end that utilizes Yum to perform the actual transactions, such as installing and removing packages, etc.
Table 2.1. PackageKit GUI Windows, Menu Locations, and Shell Prompt Commands
| Window Title | Function | How to Open | Shell Command |
|---|---|---|---|
| Add/Remove Software | Install, remove or view package info |
From the GNOME panel: → →
| gpk-application |
| Software Update | Perform package updates |
From the GNOME panel: → →
| gpk-update-viewer |
| Software Sources | Enable and disable Yum repositories |
From Add/Remove Software: →
| gpk-repo |
| Software Log Viewer | View the transaction log |
From Add/Remove Software: →
| gpk-log |
| Software Update Preferences | Set PackageKit preferences | gpk-prefs | |
| (Notification Area Alert) | Alerts you when updates are available |
From the GNOME panel: → → , Startup Programs tab
| gpk-update-icon |
packagekitd daemon runs outside the user session and communicates with the various graphical front ends. The packagekitd daemon[2] communicates via the DBus system message bus with another back end, which utilizes Yum's Python API to perform queries and make changes to the sytem. On Linux systems other than Red Hat and Fedora, packagekitd
can communicate with other back ends that are able to utilize the
native package manager for that system. This modular architecture
provides the abstraction necessary for the graphical interfaces to work
with many different package managers to perform essentially the same
types of package management tasks. Learning how to use the PackageKit
front ends means that you can use the same familiar graphical interface
across many different Linux distributions, even when they utilize a
native package manager other than Yum.
packagekitd daemon, which runs outside of the user session.
gnome-packagekit package instead of by PackageKit and its dependencies. Users working in a KDE environment may prefer to install the kpackagekit package, which provides a KDE interface for PackageKit.
pkcon.
2.4. Additional Resources
- PackageKit home page — http://www.packagekit.org/index.html
- Information about and mailing lists for PackageKit.
- PackageKit FAQ — http://www.packagekit.org/pk-faq.html
- An informative list of Frequently Asked Questions for the PackageKit software suite.
- PackageKit Feature Matrix — http://www.packagekit.org/pk-matrix.html
- Cross-reference PackageKit-provided features with the long list of package manager back ends.
[2]
System daemons are typically long-running processes that provide
services to the user or to other programs, and which are started, often
at boot time, by special initialization scripts (often shortened to init scripts). Daemons respond to the service command and can be turned on or off permanently by using the chkconfig on or chkconfig offcommands. They can typically be recognized by a “d ” appended to their name, such as the packagekitd daemon. Refer to Chapter 7, Controlling Access to Services for information about system services.
Chapter 3. RPM
Use Yum Instead of RPM Whenever Possible
Important
x86_64.rpm.
.tar.gz files.
Note
3.1. RPM Design Goals
- Upgradability
- With RPM, you can upgrade individual components of your system without completely reinstalling. When you get a new release of an operating system based on RPM, such as Red Hat Enterprise Linux, you do not need to reinstall a fresh copy of the operating system your machine (as you might need to with operating systems based on other packaging systems). RPM allows intelligent, fully-automated, in-place upgrades of your system. In addition, configuration files in packages are preserved across upgrades, so you do not lose your customizations. There are no special upgrade files needed to upgrade a package because the same RPM file is used to both install and upgrade the package on your system.
- Powerful Querying
- RPM is designed to provide powerful querying options. You can perform searches on your entire database for packages or even just certain files. You can also easily find out what package a file belongs to and from where the package came. The files an RPM package contains are in a compressed archive, with a custom binary header containing useful information about the package and its contents, allowing you to query individual packages quickly and easily.
- System Verification
- Another powerful RPM feature is the ability to verify packages. If you are worried that you deleted an important file for some package, you can verify the package. You are then notified of anomalies, if any—at which point you can reinstall the package, if necessary. Any configuration files that you modified are preserved during reinstallation.
- Pristine Sources
- A crucial design goal was to allow the use of pristine software sources, as distributed by the original authors of the software. With RPM, you have the pristine sources along with any patches that were used, plus complete build instructions. This is an important advantage for several reasons. For instance, if a new version of a program is released, you do not necessarily have to start from scratch to get it to compile. You can look at the patch to see what you might need to do. All the compiled-in defaults, and all of the changes that were made to get the software to build properly, are easily visible using this technique.The goal of keeping sources pristine may seem important only for developers, but it results in higher quality software for end users, too.
3.2. Using RPM
rpm --help or man rpm. You can also refer to Section 3.5, “Additional Resources” for more information on RPM.
3.2.1. Finding RPM Packages
- The initial RPM repositories provided with the YUM package manager . Refer to Chapter 1, Yum for details on how to use the official Red Hat Enterprise Linux package repositories.
- The Extra Packages for Enterprise Linux (EPEL) is a community effort to provide high-quality add-on packages for Red Hat Enterprise Linux . Refer to http://fedoraproject.org/wiki/EPEL for details on EPEL RPM packages.
- Unofficial, third-party repositories not ahffiliated Red Hat also provide RPM packages.
Important
When considering third-party repositories for use with your Red Hat Enterprise Linux system, pay close attention to the repository's web site with regard to package compatibility before adding the repository as a package source. Alternate package repositories may offer different, incompatible versions of the same software, including packages already included in the Red Hat Enterprise Linux repositories. - The Red Hat Errata Page, available at http://www.redhat.com/apps/support/errata/
3.2.2. Installing and Upgrading
tree-1.5.3-2.el6.x86_64.rpm. The file name includes the package name (tree), version (1.5.3), release (2), operating system major version (el6) and CPU architecture (x86_64).
rpm's -U option to:
- upgrade an existing but older package on the system to a newer version, or
- install the package even if an older version is not already installed.
rpm -U <rpm_file> is able to perform the function of either upgrading or installing as is appropriate for the package.
tree-1.5.3-2.el6.x86_64.rpm
package is in the current directory, log in as root and type the
following command at a shell prompt to either upgrade or install the tree package as determined by rpm:
rpm -Uvh tree-1.5.3-2.el6.x86_64.rpmUse -Uvh for nicely-formatted RPM installs
-v and -h options (which are combined with -U) cause rpm to print more verbose output and display a progress meter using hash signs.
Preparing... ########################################### [100%] 1:tree ########################################### [100%]
Always use the -i (install) option to install new kernel packages!
rpm provides two different options for installing packages: the aforementioned -U option (which historically stands for upgrade), and the -i option, historically standing for install. Because the -U option subsumes both install and upgrade functions, we recommend to use rpm -Uvh with all packages except kernel packages.
-i option to simply install a new kernel package instead of upgrading it. This is because using the -U
option to upgrade a kernel package removes the previous (older) kernel
package, which could render the system unable to boot if there is a
problem with the new kernel. Therefore, use the rpm -i <kernel_package> command to install a new kernel without replacing any older kernel packages. For more information on installing kernel packages, refer to Chapter 23, Manually Upgrading the Kernel.
error: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA256 signature: BAD, key ID d22e77f2
error: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA256 signature: BAD, key ID d22e77f2
NOKEY:
warning: tree-1.5.3-2.el6.x86_64.rpm: Header V3 RSA/SHA1 signature: NOKEY, key ID 57bbccba
3.2.2.1. Package Already Installed
Preparing... ########################################### [100%] package tree-1.5.3-2.el6.x86_64 is already installed
--replacepkgs option, which tells RPM to ignore the error:
rpm -Uvh --replacepkgs tree-1.5.3-2.el6.x86_64.rpm3.2.2.2. Conflicting Files
Preparing... ################################################## file /usr/bin/foobar from install of foo-1.0-1.el6.x86_64 conflicts with file from package bar-3.1.1.el6.x86_64
--replacefiles option:
rpm -Uvh --replacefiles foo-1.0-1.el6.x86_64.rpm3.2.2.3. Unresolved Dependency
error: Failed dependencies: bar.so.3()(64bit) is needed by foo-1.0-1.el6.x86_64
rpm -Uvh foo-1.0-1.el6.x86_64.rpm bar-3.1.1.el6.x86_64.rpmPreparing... ########################################### [100%] 1:foo ########################################### [ 50%] 2:bar ########################################### [100%]
--whatprovides option to determine which package contains the required file.
rpm -q --whatprovides "bar.so.3"bar.so.3 is in the RPM database, the name of the package is displayed:
bar-3.1.1.el6.i586.rpm
Warning: Forcing Package Installation
rpm to install a package that gives us a Failed dependencies error (using the --nodeps option), this is not recommended, and will usually result in the installed package failing to run. Installing or removing packages with rpm --nodeps
can cause applications to misbehave and/or crash, and can cause serious
package management problems or, possibly, system failure. For these
reasons, it is best to heed such warnings; the package manager—whether RPM, Yum or PackageKit—shows us these warnings and suggests possible fixes because accounting for dependencies is critical. The Yum
package manager can perform dependency resolution and fetch
dependencies from online repositories, making it safer, easier and
smarter than forcing rpm to carry out actions without regard to resolving dependencies.
3.2.3. Configuration File Changes
saving /etc/foo.conf as /etc/foo.conf.rpmsave
foo.conf.rpmnew,
and leave the configuration file you modified untouched. You should
still resolve any conflicts between your modified configuration file and
the new one, usually by merging changes from the old one to the new one
with a diff program.
package foo-2.0-1.el6.x86_64.rpm (which is newer than foo-1.0-1) is already installed
--oldpackage option:
rpm -Uvh --oldpackage foo-1.0-1.el6.x86_64.rpm3.2.4. Uninstalling
rpm -e foo
Note
foo, not the name of the original package file, foo-1.0-1.el6.x86_64. If you attempt to uninstall a package using the rpm -e command and the original full file name, you will receive a package name error.
rpm -e ghostscript
error: Failed dependencies:
libgs.so.8()(64bit) is needed by (installed) libspectre-0.2.2-3.el6.x86_64
libgs.so.8()(64bit) is needed by (installed) foomatic-4.0.3-1.el6.x86_64
libijs-0.35.so()(64bit) is needed by (installed) gutenprint-5.2.4-5.el6.x86_64
ghostscript is needed by (installed) printer-filters-1.1-4.el6.noarch<library_name>.so.<number> ~]# rpm -q --whatprovides "libgs.so.8()(64bit)"
ghostscript-8.70-1.el6.x86_64Warning: Forcing Package Installation
rpm to remove a package that gives us a Failed dependencies error (using the --nodeps option), this is not recommended, and may cause harm to other installed applications. Installing or removing packages with rpm --nodeps
can cause applications to misbehave and/or crash, and can cause serious
package management problems or, possibly, system failure. For these
reasons, it is best to heed such warnings; the package manager—whether RPM, Yum or PackageKit—shows us these warnings and suggests possible fixes because accounting for dependencies is critical. The Yum
package manager can perform dependency resolution and fetch
dependencies from online repositories, making it safer, easier and
smarter than forcing rpm to carry out actions without regard to resolving dependencies.
3.2.5. Freshening
rpm -Fvh foo-2.0-1.el6.x86_64.rpm*.rpm glob:
rpm -Fvh *.rpm3.2.6. Querying
/var/lib/rpm/,
and is used to query what packages are installed, what versions each
package is, and to calculate any changes to any files in the package
since installation, among other use cases.
-q option. The rpm -q package name command displays the package name, version, and release number of the installed package <package_name>. For example, using rpm -q tree to query installed package tree might generate the following output:
tree-1.5.2.2-4.el6.x86_64
man rpm for details) to further refine or qualify your query:
-a— queries all currently installed packages.-f— queries the RPM database for which package owns<file_name><file_name>rpm -qfinstead of/bin/lsrpm -qf ls).-p— queries the uninstalled package<package_file><package_file>
-idisplays package information including name, description, release, size, build date, install date, vendor, and other miscellaneous information.-ldisplays the list of files that the package contains.-sdisplays the state of all the files in the package.-ddisplays a list of files marked as documentation (man pages, info pages, READMEs, etc.) in the package.-cdisplays a list of files marked as configuration files. These are the files you edit after installation to adapt and customize the package to your system (for example,sendmail.cf,passwd,inittab, etc.).
-v to the command to display the lists in a familiar ls -l format.
3.2.7. Verifying
rpm -V verifies a package. You can use any of the Verify Options listed for querying to specify the packages you wish to verify. A simple use of verifying is rpm -V tree, which verifies that all the files in the tree package are as they were when they were originally installed. For example:
- To verify a package containing a particular file:
rpm -Vf /usr/bin/treeIn this example,/usr/bin/treeis the absolute path to the file used to query a package. - To verify ALL installed packages throughout the system (which will take some time):
rpm -Va - To verify an installed package against an RPM package file:
rpm -Vp tree-1.5.3-2.el6.x86_64.rpmThis command can be useful if you suspect that your RPM database is corrupt.
c"
denotes a configuration file) and then the file name. Each of the eight
characters denotes the result of a comparison of one attribute of the
file to the value of that attribute recorded in the RPM database. A
single period (.) means the test passed. The following characters denote specific discrepancies:
5— MD5 checksumS— file sizeL— symbolic linkT— file modification timeD— deviceU— userG— groupM— mode (includes permissions and file type)?— unreadable file (file permission errors, for example)
3.3. Checking a Package's Signature
<rpm_file> is the file name of the RPM package):
rpm -K --nosignature <rpm_file> <rpm_file>: rsa sha1 (md5) pgp md5 OK-K with -Kvv in the command.
x files as well.
3.3.1. Importing Keys
rpm --import /usr/share/rhn/RPM-GPG-KEYrpm -qa gpg-pubkey*gpg-pubkey-db42a60e-37ea5438
rpm -qi followed by the output from the previous command:
rpm -qi gpg-pubkey-db42a60e-37ea54383.3.2. Verifying Signature of Packages
<rpm-file> with the filename of the RPM package):
rpm -K <rpm-file> md5 gpg OK.
This means that the signature of the package has been verified, that it
is not corrupt, and therefore is safe to install and use.
3.4. Practical and Common Examples of RPM Usage
- Perhaps you have deleted some files by accident, but you are not sure what you deleted. To verify your entire system and see what might be missing, you could try the following command:
rpm -VaIf some files are missing or appear to have been corrupted, you should probably either re-install the package or uninstall and then re-install the package. - At some point, you might see a file that you do not recognize. To find out which package owns it, enter:
rpm -qf /usr/bin/ghostscriptThe output would look like the following:ghostscript-8.70-1.el6.x86_64
- We can combine the above two examples in the following scenario. Say you are having problems with
/usr/bin/paste. You would like to verify the package that owns that program, but you do not know which package ownspaste. Enter the following command,rpm -Vf /usr/bin/pasteand the appropriate package is verified. - Do you want to find out more information about a particular program? You can try the following command to locate the documentation which came with the package that owns that program:
rpm -qdf /usr/bin/freeThe output would be similar to the following:/usr/share/doc/procps-3.2.8/BUGS /usr/share/doc/procps-3.2.8/FAQ /usr/share/doc/procps-3.2.8/NEWS /usr/share/doc/procps-3.2.8/TODO /usr/share/man/man1/free.1.gz /usr/share/man/man1/pgrep.1.gz /usr/share/man/man1/pkill.1.gz /usr/share/man/man1/pmap.1.gz /usr/share/man/man1/ps.1.gz /usr/share/man/man1/pwdx.1.gz /usr/share/man/man1/skill.1.gz /usr/share/man/man1/slabtop.1.gz /usr/share/man/man1/snice.1.gz /usr/share/man/man1/tload.1.gz /usr/share/man/man1/top.1.gz /usr/share/man/man1/uptime.1.gz /usr/share/man/man1/w.1.gz /usr/share/man/man1/watch.1.gz /usr/share/man/man5/sysctl.conf.5.gz /usr/share/man/man8/sysctl.8.gz /usr/share/man/man8/vmstat.8.gz
- You may find a new RPM, but you do not know what it does. To find information about it, use the following command:
rpm -qip crontabs-1.10-32.1.el6.noarch.rpmThe output would be similar to the following:Name : crontabs Relocations: (not relocatable) Version : 1.10 Vendor: Red Hat, Inc. Release : 32.1.el6 Build Date: Thu 03 Dec 2009 02:17:44 AM CET Install Date: (not installed) Build Host: js20-bc1-11.build.redhat.com Group : System Environment/Base Source RPM: crontabs-1.10-32.1.el6.src.rpm Size : 2486 License: Public Domain and GPLv2 Signature : RSA/8, Wed 24 Feb 2010 08:46:13 PM CET, Key ID 938a80caf21541eb Packager : Red Hat, Inc. <http://bugzilla.redhat.com/bugzilla> Summary : Root crontab files used to schedule the execution of programs Description : The crontabs package contains root crontab files and directories. You will need to install cron daemon to run the jobs from the crontabs. The cron daemon such as cronie or fcron checks the crontab files to see when particular commands are scheduled to be executed. If commands are scheduled, it executes them. Crontabs handles a basic system function, so it should be installed on your system.
- Perhaps you now want to see what files the
crontabsRPM package installs. You would enter the following:rpm -qlp crontabs-1.10-32.1.el6.noarch.rpmThe output is similar to the following:/etc/cron.daily /etc/cron.hourly /etc/cron.monthly /etc/cron.weekly /etc/crontab /usr/bin/run-parts /usr/share/man/man4/crontabs.4.gz
3.5. Additional Resources
3.5.1. Installed Documentation
rpm --help— This command displays a quick reference of RPM parameters.man rpm— The RPM man page gives more detail about RPM parameters than therpm --helpcommand.
3.5.2. Useful Websites
- The RPM website — http://www.rpm.org/
- The RPM mailing list can be subscribed to, and its archives read from, here — https://lists.rpm.org/mailman/listinfo/rpm-list